Overview
In today’s digital economy, one’s biggest asset is data and the insight and knowledge it provides. It naturally follows that securing such data is essential to the growth and sustenance of any organization. Cybercrime is on an exponential rise and it is estimated that it will cost the world $10.5 Trillion annually by 2025. A recent study concluded that there is a hacker attack every 39 seconds around the world and that approximately 8 billion records of data are compromised every year. Such alarming statistics show an incontestable need for Cybersecurity measures to protect data, systems, and networks from hackers.
Here are some common methods that threaten Cyber Security:
- Malware Most common form of cyber-attack that enters system via email, attachment, download.
- Virus A Program that attaches itself to clean or infects the files and spread through the systems.
- Trojans A virus disguised as legitimate software, enters systems, and collects the data.
- Spyware Secretly records actions of the users, this can steal vital information like credit card details.
- Ransomware This locks systems or files and threatens to erase files unless ransom is paid.
- Adware Malware that spreads through advertisements.
- SQL Injection Exploits vulnerabilities of data driven applications by inserting malicious through SQL statements.
Phishing: Sending a mail which contains malicious links to user disguising as an organization in which user is working, this can steal personal and organization data.
Man in middle attack: Intercepting in communication between 2 persons to steal data, this often happens over an unsecured Wi-Fi network.
Denial of service attack: Preventing computer system or server from serving the user requests by loading the server with unnecessary traffic thus hampering the day-to-day work of the organization.
Business Problem Statement
Today, phishing accounts for 90% of all breaches that organizations face, they have grown 65% over the last year, and they account for over $12 Billion in business losses.
Given that we live in an increasingly connected world, the stakes of a cyber security attack are higher than ever – at an individual level it can result in losing personal data like family photos and at an organization level – it can result in the loss of vital information about the company. Though researchers continually investigate new and emerging security threats, there is always a new vulnerability exposed which could result in massive damage to the organization. Defending oneself from a cyber security attack is not only the responsibility of organization, but that of every individual must feel equally responsible for the security, often these attacks might enter the system through an individual mail.
Employees of a multinational company have been receiving phishing emails. These emails are very well organized causing even the most experienced employees to fall for it, resulting in them providing vital personal and professional information.
For example, the phishing email asks users to change their password claiming that the password is expiring. Users, who are unaware that this is a phishing email, then provide their old and new passwords as well as email ID which exposes their current password to the external world.
To tackle this risk, the client organization geared up to run a campaign to increase cyber security awareness to their employees. As part of this campaign, the organization itself sends a phishing mails to see which employees are falling for these phishing attacks by clicking on the links from unknown senders. These campaigns are run regularly – once in every quarter. Users will be educated when they first fall for the fake phishing mail, and if the same users repeat it in the follow up campaigns, stringent actions will be taken.
However, the organization has no way of meaningfully collecting and reading such data. It has no means to measure the performance of their campaigns.
Solutioning & Best Practices Implemented
For these campaigns that run erratically every quarter, we developed a dashboard that would help in getting these insights for management consumption. This is useful in identifying the users who are continuously falling prey for these phishing mails. Dashboard is mainly categorized into two sections, namely Training and Phishing. The client can understand the total users by region, unction/department, and reporting manager.
These insights have saved a lot of man hours in the form of training only for required users who are falling prey to these phishing attacks, also, easy to identify the repeated users who are falling for the phishing mails.
- Mail should be as clear as a genuine mail from organization
- Users should be trained to understand the mail like checking from address, not to click any link from unsolicited mails
- Mails should be deceiving like update VPN, Password
- Mails like “You have won a lottery” is sent to spam by mail server, should avoid using such phrases
- Only a set of selected users from all departments and from different geographical locations will be receiving mail in a campaign, sending a fake phishing mail to everyone in an organization at same time isn’t a good idea
Solution Architecture Diagram
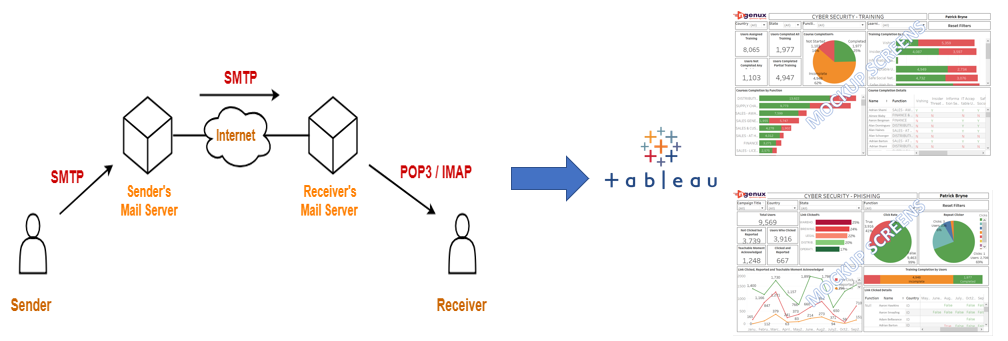
Technology/Frameworks used for Implementing the solution
- SMTP: Simple Mail Transfer Protocol is an application that send, receive, and relay outgoing emails between senders and receivers.
- Mailing Domain:Mailing domain name should be like the one organization is using. For example, if a company uses ngenux.com, then the mailing domain should be something like ngenuxmail.com, ngenuxadmin.com.
- SQL Server: Used in storing and retrieving data, when user clicks the link the details of employee such as Employee ID, Email, Campaign Name, time of click can be used for analytics at later point of time.
- Tableau: Used for running analytics and building visualizations.
Key Performance Indicators
- Total Users: Number of users to whom phishing mail has been disbursed.
- Not clicked but reported: Users who has identified it as phishing mail and has reported.
- Users who clicked: Users who failed to identify as phishing mail, needs to undergo training
- Clicked and reported: Users who have clicked the link in mail and realized its a phishing mail and reported
- Click%: Percentage of users who fallen prey to phishing mail
Dashboard Screenshots
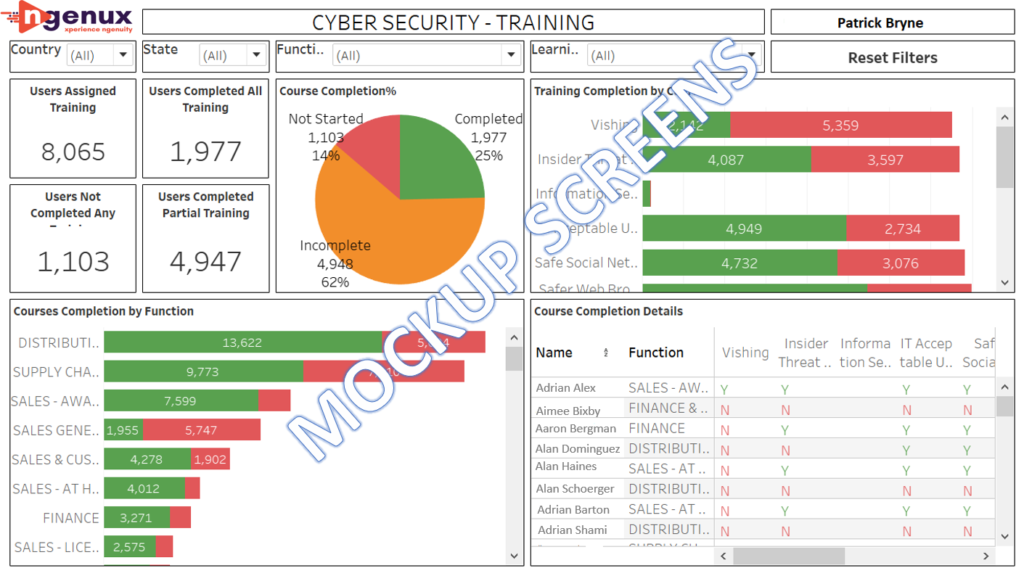
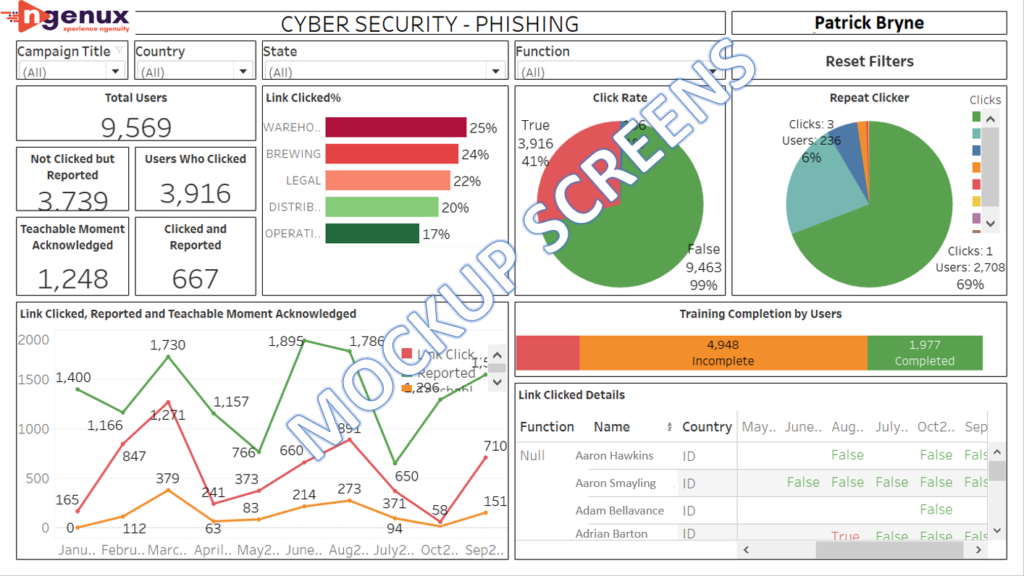
Protecting and securing data is of paramount importance. Falling for phishing attacks is an easily avoidable outcome and campaigns to test the employees of the organization are only a part of a solution. Analyzing and understanding the patterns of the users who fall for phishing attacks will greatly strengthen the organization’s defenses. At Ngenux, we provide smart solutions so you can make the most of your campaigns. Please get in touch with us at connect@ngenux.com to know more about building effective dashboards to monitor your cyber security campaigns.
